tp-link WR740漏洞复现
前言
本项目旨在复现TP-Link WR740路由器固件中的漏洞。通过对固件进行解包、扫描和分析,最终实现漏洞的验证。整个过程涉及工具的安装与使用、代码的逆向分析以及模拟环境的搭建与测试。
0.问题分析
TP-Link WR740路由器存在一个严重的安全漏洞,允许攻击者通过特定的HTTP请求执行任意命令。这个漏洞存在于httpd程序中,通过对usr和passwd参数的验证不足,攻击者可以利用默认凭证进行未授权访问并执行命令。
1.固件获取
2.binwalk解包
环境
binwalk安装
binwalk 安装
1 | $ git clone https://github.com/ReFirmLabs/binwalk.git |
sasquatch工具支持对 非标准的SquashFS格式的文件镜像 进行解压
sasquatch 安装
1 | $ sudo apt-get install build-essential liblzma-dev liblzo2-dev zlib1g-dev |
sasquatch patch
1 | cd patches |
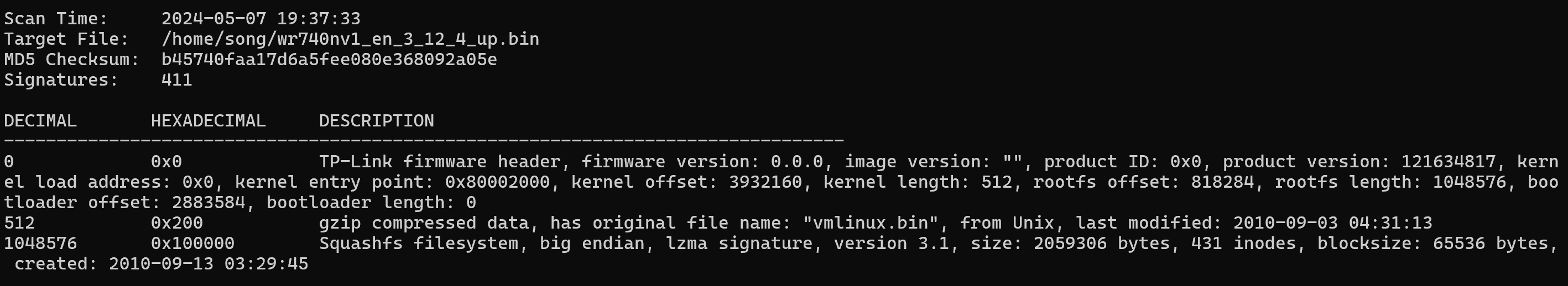
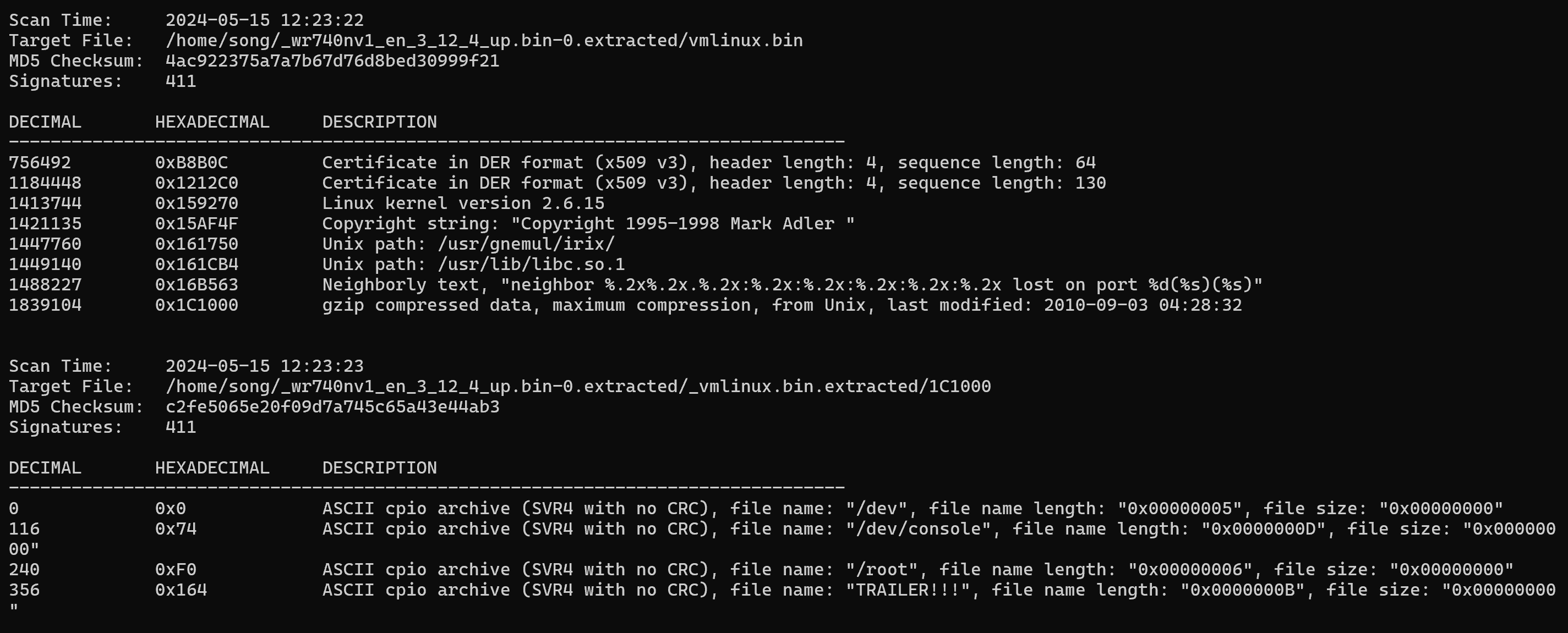
binwalk解包
$ binwalk -Me wr740nv1_en_3_12_4_up.bin
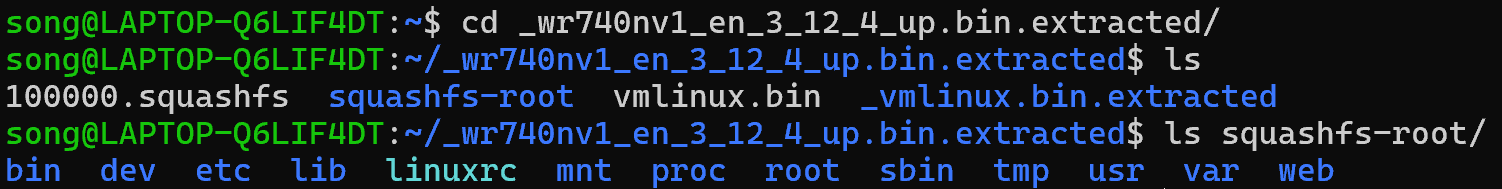
3.firmwalker扫描
获取firmwalker:git clone https://github.com/craigz28/firmwalker.git
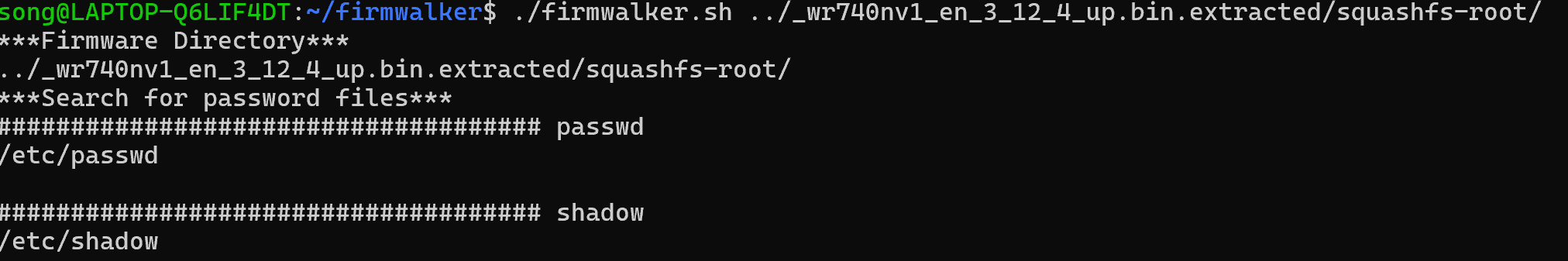
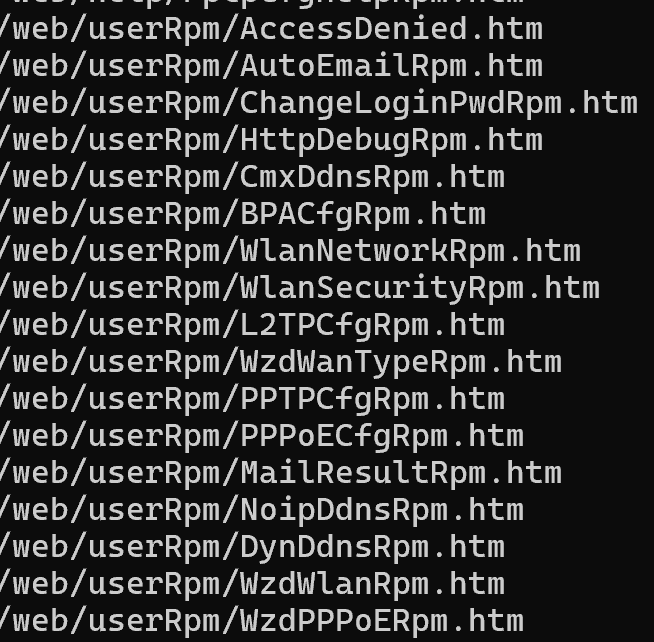
路由器Web相关URL的格式为:/web/userRpm/*
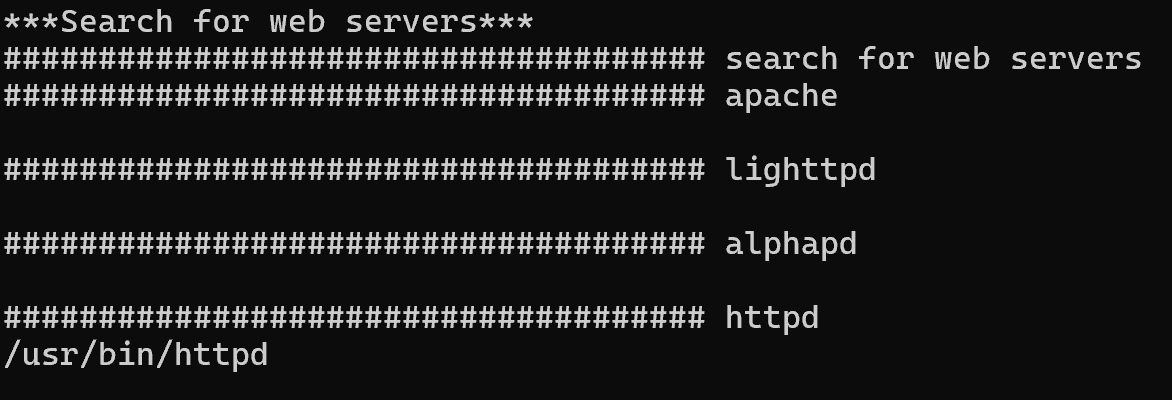
http服务器为httpd,且httpd中包含较多关键字符串,考虑对其进行分析
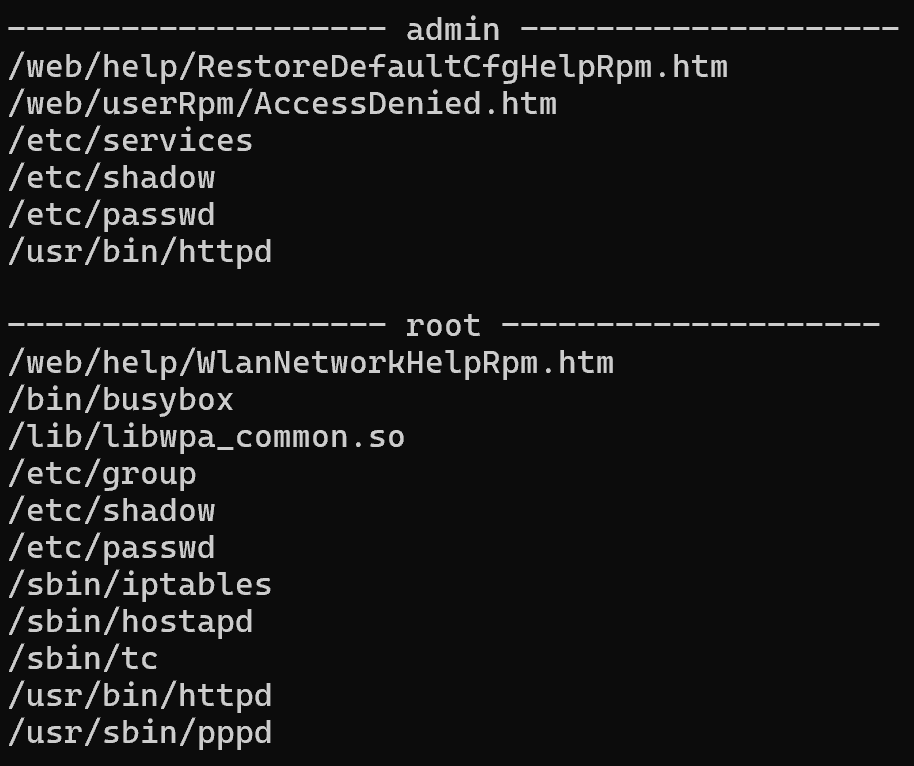
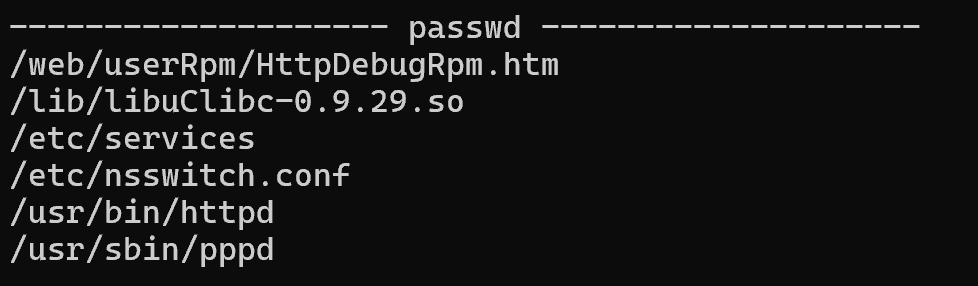
4.httpd反编译分析
使用IDA搜索passwd字符串,得到如下结果
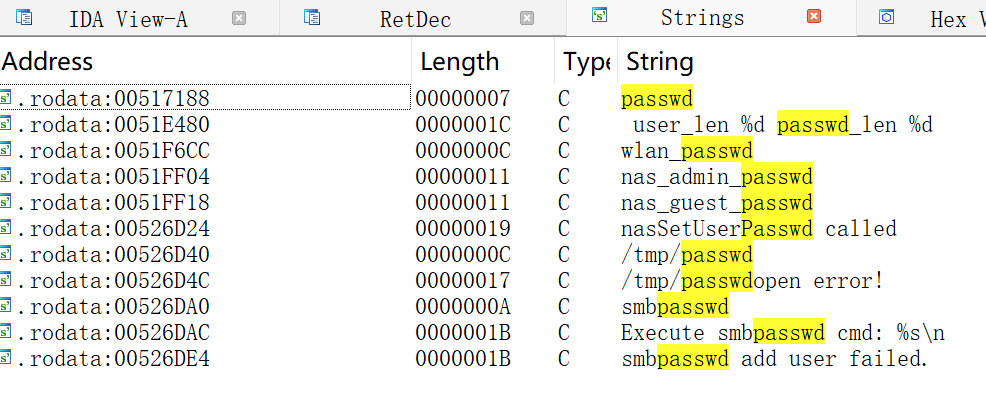
第一个搜索结果仅有passwd,比较可疑,检查其引用。
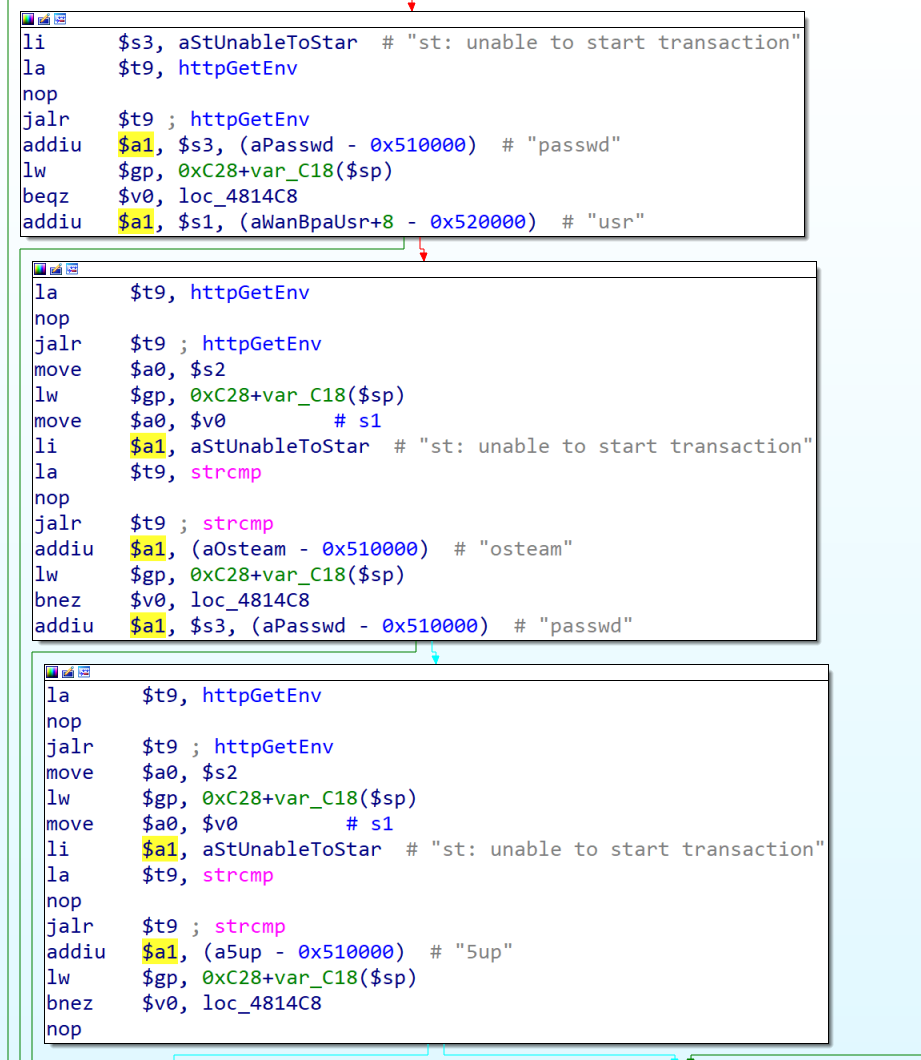
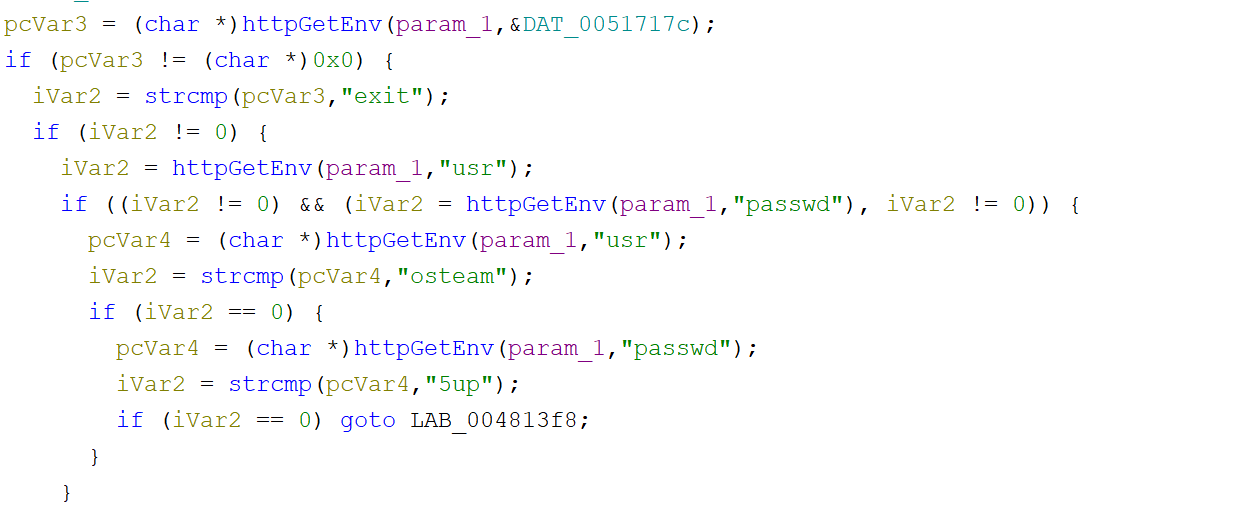
在“passwd”附近还出现了“usr”字符串,以及“osteam”、“5up”两个意义不明的字符串,考虑将整个函数转换为C代码进行分析
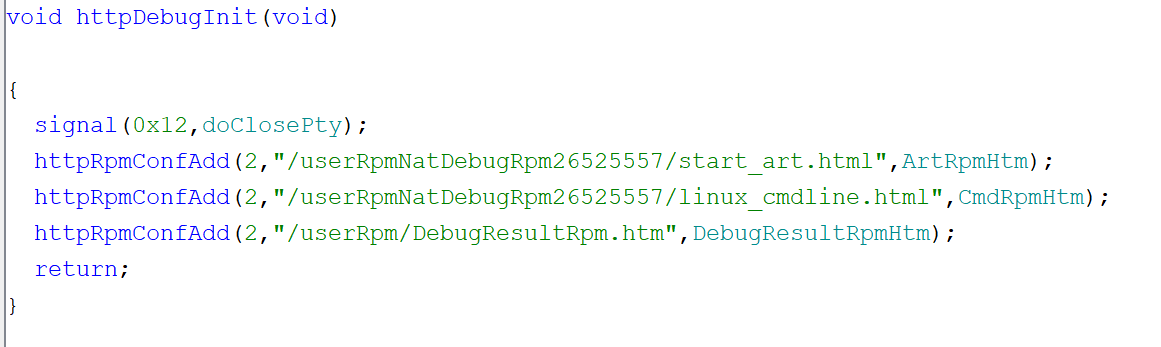
1 | int DebugResultRpmHtm(undefined4 param_1) |
注意到此函数将http请求中usr、passwd字段分别与“osteam”、“5up”比较,并执行http中cmd字段的命令
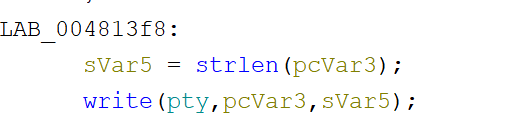
通过write(pty,cmd,strlen(cmd))来模拟执行命令。伪终端(pseudo
terminal,有时也被称为 pty)是指伪终端 master 和伪终端 slave
这一对字符设备。其中的 slave 对应
/dev/pts/目录下的一个文件,而 master
则在内存中标识为一个文件描述符(fd)。伪终端由终端模拟器提供,终端模拟器是一个运行在用户态的应用程序。可通过写pty文件执行指令。
用IDA
Pro对httpd程序进行反编译分析。搜索关键字符串如passwd,并分析相关函数,发现漏洞点在于对usr和passwd字段的验证不足,且可以通过pty伪终端执行命令。
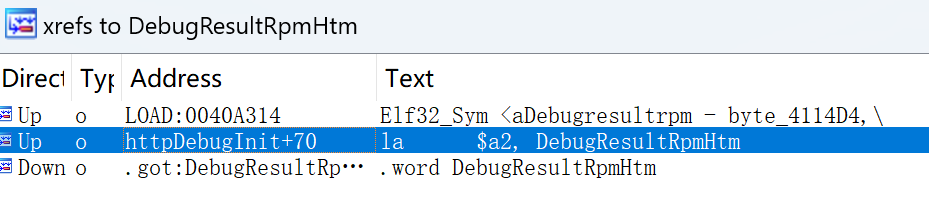
检查该函数调用情况,发现url绑定
5.模拟验证
环境
由于涉及分区挂载操作,FirmAE不能在WSL下运行。
FirmAE安装
1 | $ git clone --recursive https://github.com/pr0v3rbs/FirmAE |
模拟
先检查能否模拟
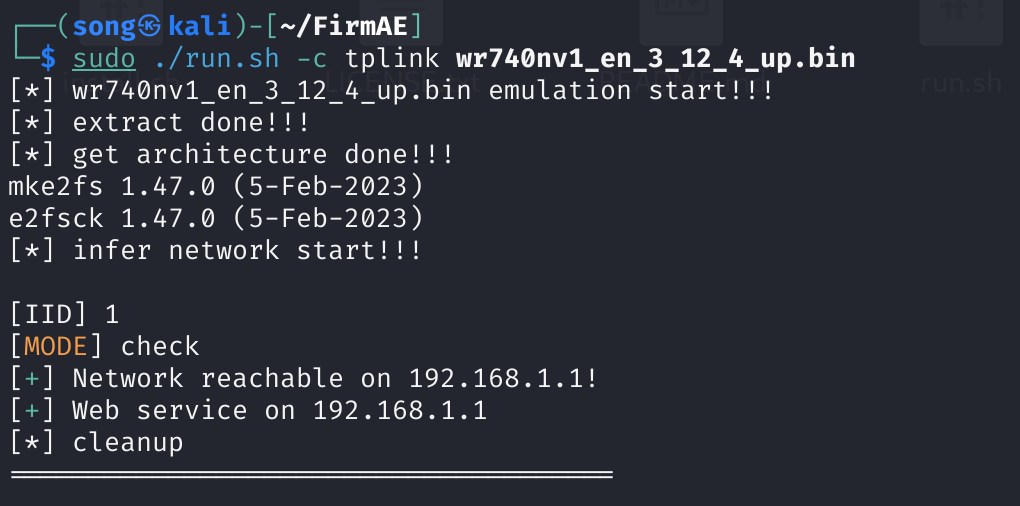
然后进行模拟
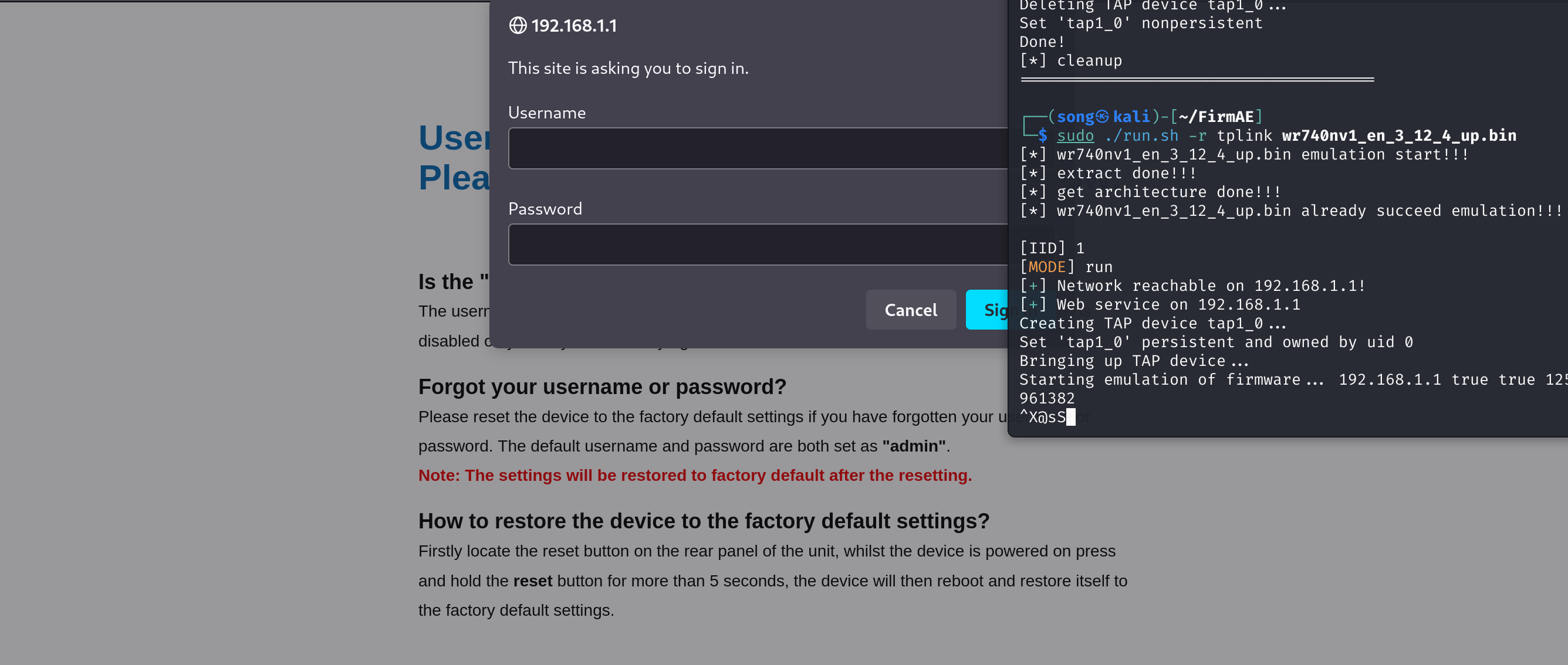
访问前面发现的url,根据提示输入默认账号密码,发现可以执行命令
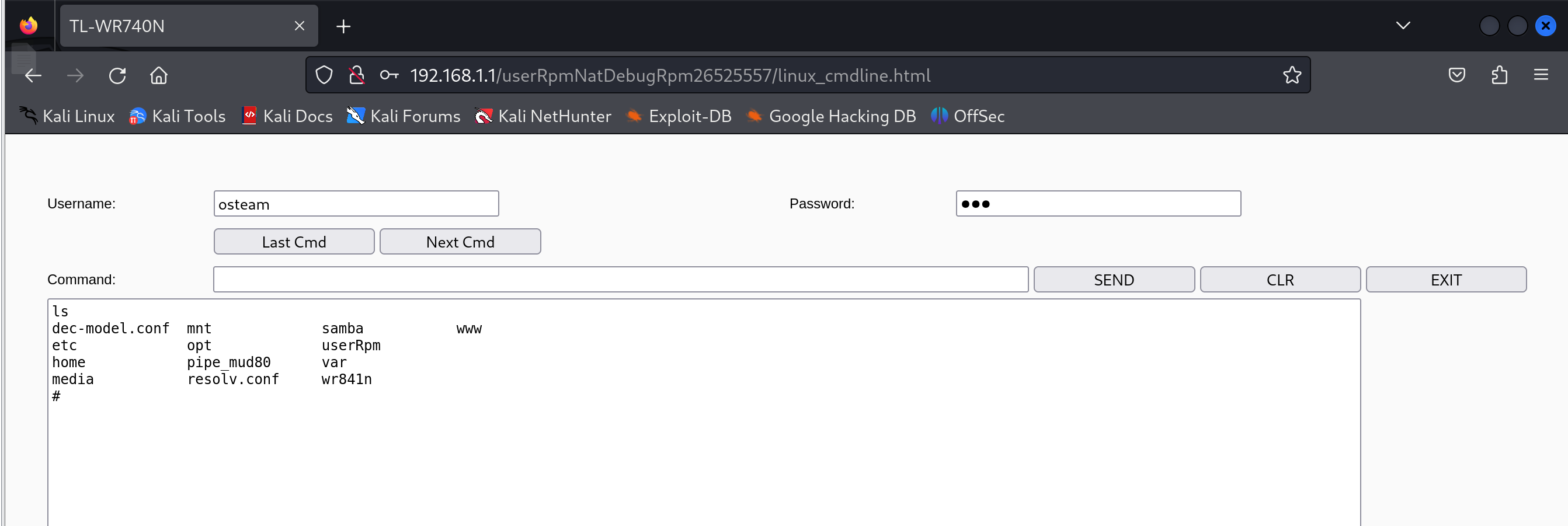
6. 结论
通过对TP-Link WR740路由器固件的详细分析与模拟测试,成功复现了固件中的漏洞。本文展示了从固件获取、解包、扫描到漏洞分析和模拟验证的全过程,为进一步的安全研究提供了实践案例。
7. 参考文献
- Binwalk GitHub Repository: https://github.com/ReFirmLabs/binwalk
- Firmwalker GitHub Repository: https://github.com/craigz28/firmwalker
- FirmAE GitHub Repository: https://github.com/pr0v3rbs/FirmAE
- TP-Link WR740 后门漏洞复现(学习记录):TP-Link WR740 后门漏洞复现(学习记录)-智能设备-看雪-安全社区|安全招聘|kanxue.com
tp-link WR740漏洞复现